FBI Warning: BADBOX 2.0 Malware Infects Over 1 Million IoT Devices
Introduction
The FBI has issued a critical warning about BADBOX 2.0, a malware campaign that has compromised over 1 million Internet-connected devices. This botnet transforms consumer-grade electronics into residential proxies used for criminal purposes, including ad fraud and credential stuffing. The majority of these infected devices originate from Chinese Android-based platforms such as smart TVs, streaming boxes, projectors, and tablets.
How BADBOX 2.0 Malware Works
Devices infected with BADBOX 2.0 often come with malware pre-installed or are compromised through firmware updates and malicious Android apps. These apps sometimes sneak past security checks on Google Play and third-party app stores. The malware grants attackers unauthorized access during the initial setup or app installation phase. Consequently, home networks become vulnerable to malicious use once these devices go online.
Malicious Capabilities of the BADBOX 2.0 Botnet
- Residential Proxy Networks: It redirects cybercriminal traffic through victims’ IP addresses to hide malicious activities.
- Ad Fraud: The malware loads and clicks on ads in the background, generating revenue for threat actors.
- Credential Stuffing: By masking attacker IPs, it facilitates attempts to access accounts using stolen credentials.
Evolution and Global Reach of BADBOX 2.0
The original BADBOX malware surfaced in 2023, hidden in cheap Android TV boxes like the T95. Although Germany’s cybersecurity agency disrupted part of the botnet in 2024, the threat rapidly returned. Within a week, researchers identified 192,000 newly infected devices, including mainstream brands such as Yandex TVs and Hisense smartphones.
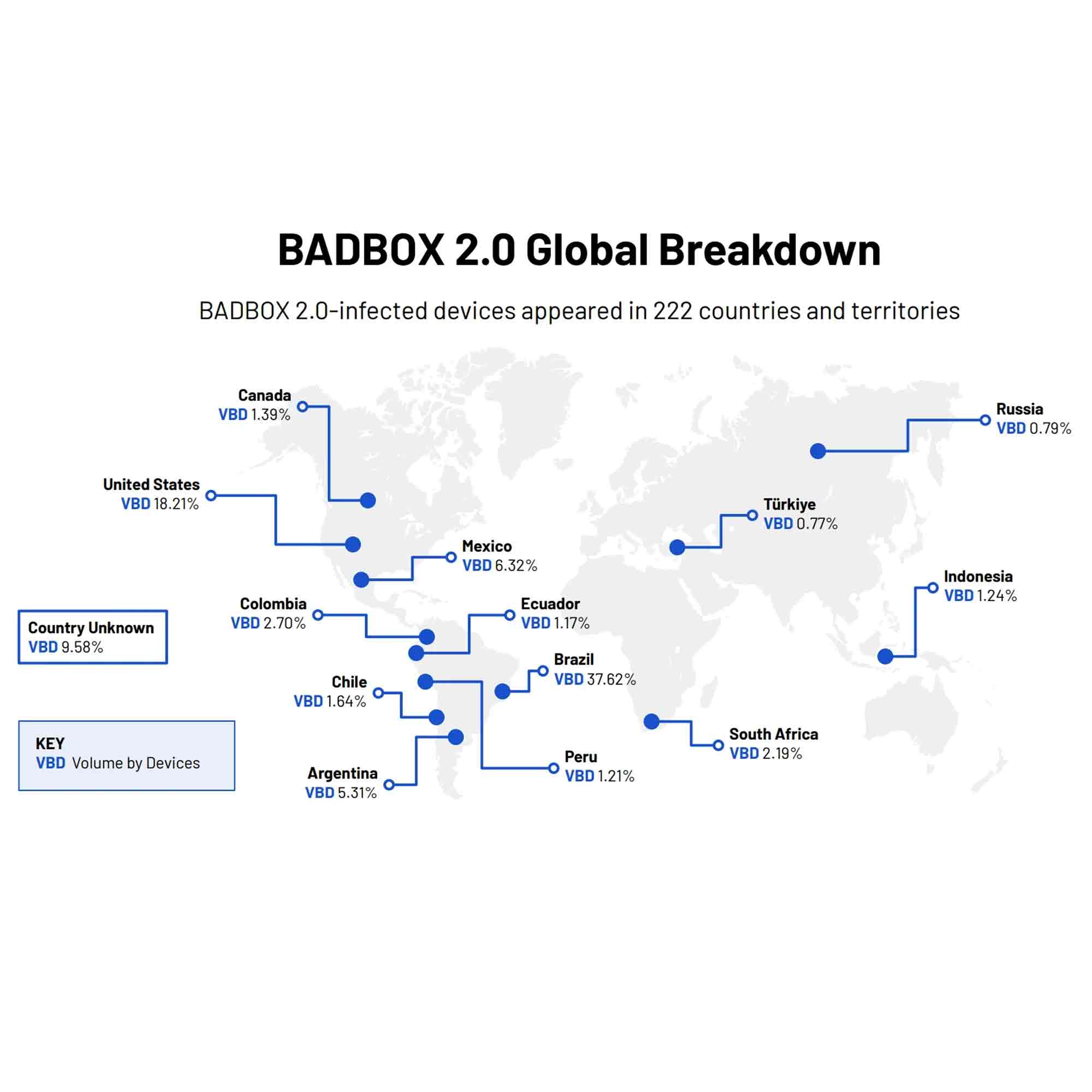
According to HUMAN’s Satori Threat Intelligence, BADBOX 2.0 is more pervasive than ever, infecting over 1 million devices by March 2025. These devices, built using the Android Open Source Project, are not Google Play Protect certified, making them more vulnerable to malware infiltration. HUMAN observed BADBOX 2.0 traffic in 222 countries and territories globally, with Brazil (37.6%), the United States (18.2%), Mexico (6.3%), and Argentina (5.3%) showing the highest infection rates.
Countermeasures and Ongoing Risk
Infected Device Models
The following Android-based devices are confirmed to be infected by the BADBOX 2.0 malware. Many are uncertified, low-cost imports often found on unofficial marketplaces:
| Device Model | Device Model | Device Model | Device Model |
|---|---|---|---|
| TV98 | X96Q_Max_P | Q96L2 | X96Q2 |
| X96mini | S168 | ums512_1h10_Natv | X96_S400 |
| X96mini_RP | TX3mini | HY-001 | MX10PRO |
| X96mini_Plus1 | LongTV_GN7501E | Xtv77 | NETBOX_B68 |
| X96Q_PR01 | AV-M9 | ADT-3 | OCBN |
| X96MATE_PLUS | KM1 | X96Q_PRO | Projector_T6P |
| X96QPRO-TM | sp7731e_1h10_native | M8SPROW | TV008 |
| X96Mini_5G | Q96MAX | OrbsMart_TR43 | Z6 |
| TVBOX | Smart | KM9PRO | A15 |
| Transpeed | KM7 | iSinbox | I96 |
| SMART_TV | Fujicom-SmartTV | MXQ9PRO | MBOX |
| X96Q | iSinbox | Mbox | R11 |
| GameBox | KM6 | X96Max_Plus2 | TV007 |
| Q9 Stick | SP7731E | H6 | X88 |
| X98K | TXCZ |
Despite a second disruption effort by HUMAN in collaboration with Google, Trend Micro, and The Shadowserver Foundation, BADBOX 2.0 continues to spread. Over 500,000 infected devices were blocked from communicating with command and control servers, yet new infections persist as compromised devices remain on the market.
How to Identify and Mitigate BADBOX 2.0
Common indicators of infection include:
- Presence of unauthorized app marketplaces
- Disabled Google Play Protect settings
- TV boxes advertised for free or “unlocked” streaming
- Devices from unknown or off-brand manufacturers
- Unusual network traffic patterns
Most infected devices are uncertified and not protected by Google’s Play Protect program. As a result, users are highly encouraged to assess their home networks thoroughly.
FBI Recommendations to Protect Your Home Network
The FBI recommends several proactive measures to defend against BADBOX 2.0:
- Audit all IoT devices for unusual activity
- Avoid downloading apps from unofficial sources
- Monitor network traffic continuously
- Update all connected devices with the latest firmware
- Isolate any suspicious device from your network immediately
Conclusion
BADBOX 2.0 represents a persistent and evolving threat that exploits consumer electronics for large-scale cybercriminal operations. Although security agencies and private-sector partners have successfully disrupted portions of the botnet, ongoing vigilance is essential. Consumers should verify the origin and security of IoT devices and remain cautious about software sources.
For a deeper defense-in-depth approach, check out our guide on setting up your own encrypted VPN server in 15 minutes, which can safeguard your network alongside measures to block malware like BADBOX 2.0 or read more on Trend Micro’s threat intelligence.